18 May Hybrid Modern Authentication for Skype for Business Server & Exchange Server 2016
Hybrid Modern Authentication for Skype for Business Server & Exchange Server 2016
Detailed configuration and troubleshooting steps are covered here and here for enabling HMA for Exchange and Skype for Business respectively.
Skype for Business Server 2015 May 2017 cumulative update supports Hybrid Modern Authentication (HMA). To use HMA with SfB on-premises an on-premises Active Directory federation is required with Azure Active Directory (AAD).
HMA allows SfBS & Exchange 2013/2016 (Office 2013 +) to leverage AAD security capabilities like two-factor authentication, or Intune Modern Application Management policies. HMA offers greater security to premises based users by moving authorisation to the Microsoft Cloud but authentication remains on-premises. It also provides a unified experience and approach to authentication for users across Microsoft Office and can be granularly controlled further with Conditional Access Policies.
Skype for Business Authentication Flow
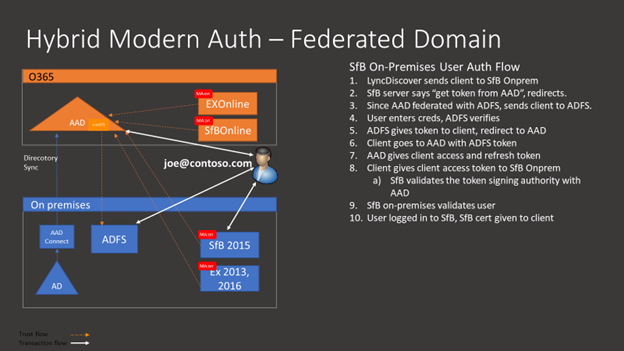
Skype for Business Authentication Flow for EWS connectivity
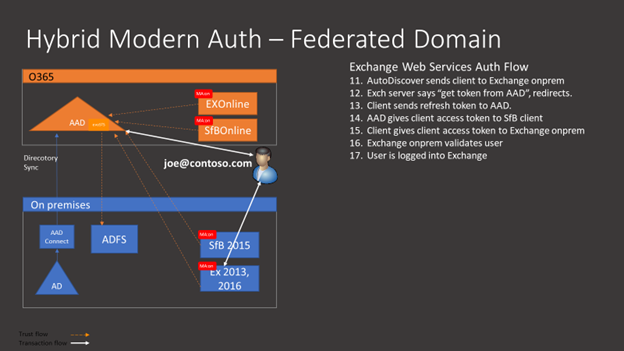
Exchange Authentication Flow
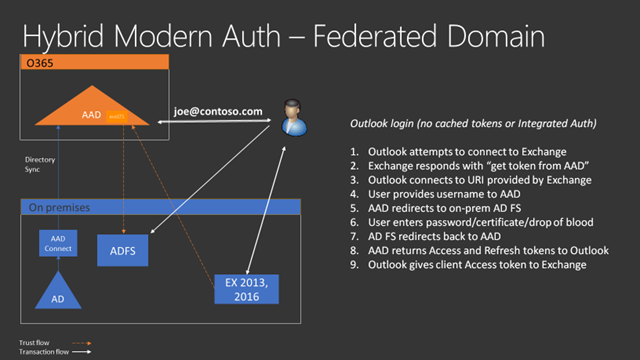
Skype for Business Server Prerequisites
- The SfB server needs to support HMA. Support for HMA is included in SfB server May 2017 CU5 release, build .281 or higher.
- The SfB server is configured to send authentication requests to Azure AAD. We do this in two steps:
- Configure evoSTS Oauth server
- Set the Oauth configuration to use this server
- SfB clients support Modern Authentication. For SfB 2016 clients, this capability will be on by default. For SfB 2013 clients, a registry entry is required > https://support.office.com/en-us/article/Enable-Modern-Authentication-for-Office-2013-on-Windows-devices-7dc1c01a-090f-4971-9677-f1b192d6c910
- Azure AAD needs to accept authentication requests from SfB clients. Since the clients will be making these requests for authentication using the on-premises web service URL’s these web service URL’s need to be configured as Service Principal Names (SPN’s) for the O365 tenant’s AAD SfB service application principal. The SPN’s need to be in the format of https://url as this is how the requests will be coming from the clients. Since clients can connect from either internal or external web service URL’s, depending on their network location, both need to be added. This needs to completed on all SfB Front End (FE) servers deployed.
- One Office 365 tenant user must be assigned a Skype for Business license in order for the service principal for the Skype for Business workload to be created in Azure AD. This does not need to be an actual production user of Skype for Business online.
- User accounts must exist in AAD.
- The SfB servers need to trust the AAD tokens presented by the clients. Therefore all FE servers need direct Internet access to login.windows.net which will allow them to periodically retrieve the AAD certificate against which they will verify the tokens presented by clients.
- Split domain hybrid should be enabled and configured.
- SfBO tenant has been enabled for MA, see here.
Exchange Server Prerequisites
- The following Identity configurations with AAD are supported
- Federated Identity with AAD with any on-premises STS supported by Office 365
- Password Hash Synchronization
- Pass Through Authentication
- The entire on-premises directory must be synchronized to AAD, and all domains used for logon must be included in the sync configuration.
- Exchange servers must be Exchange 2013 (CU19+) and/or Exchange 2016 (CU8+)
- No Exchange 2010 in the environment
- MAPI over HTTP enabled.
- OAuth must be enabled on all Virtual Directories used by Outlook (/AutoDiscover, /EWS, /Mapi, /OAB)
- Ensure AAD Connect between on-premises AD and the O365 tenant has the “Exchange hybrid deployment” setting enabled in the Optional Features settings of Azure AD Connect.
- Ensure SSL offloading is not being used between the load balancer and Exchange servers.
- Ensure all user networks can reach AAD efficiently.
- EXO tenant has been enabled for MA, see here.
Enable Hybrid Modern Authentication for SfB
- From SfB PowerShell Confirm CU5 or higher is installed with Get-CsServerPatchVersion and confirm the Front End is listed with 6.0.9319.281 or higher.
- Obtain web service URL’s with Get-CsService -WebServer | Select-Object PoolFqdn, InternalFqdn, ExternalFqdn | FL. If you any Standard Edition servers are installed, the InternalFQDN will be blank. In this case the Pool FQDN will be used for the InternalFQDN needed to define the SPN for these servers.
- Connect to AAD and configure the SPN’s for the SfB Service Principal in Azure AD by running the commands below:-
- $lync=Get-MsolServicePrincipal -AppPrincipalId 00000004-0000-0ff1-ce00-000000000000
- $lync.ServicePrincipalNames.Add(“https://labpool1webext.shuc.uk/”)
- $lync.ServicePrincipalNames.Add(“https:// labpool1.shuc.uk/”)
- $lync | Set-MsolServicePrincipal
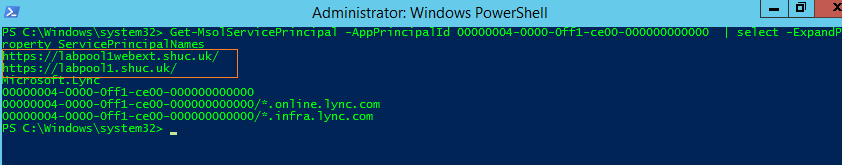
- Confirm the SPN’s are configured correctly:
Get-MsolServicePrincipal -AppPrincipalId 00000004-0000-0ff1-ce00-000000000000 | select -ExpandProperty ServicePrincipalNames
- Run Get-CsOauthConfiguration from the SfB on-premises Management Shell and make note of the current configuration as it may have been set to use an on-premises Modern Authentication for SfB using on-premises ADFS server for the Oauth Server
- Create the EvoSTS Oauth Server by running New-CsOAuthServer -Identity evoSTS -MetadataUrl https://login.windows.net/common/FederationMetadata/2007-06/FederationMetadata.xml -AcceptSecurityIdentifierInformation $true -Type AzureAd
- Cut over to HMA by setting SfB Oauth configuration to use the EvoSTS Oauth Server: Set-CsOAuthConfiguration -ClientAuthorizationOAuthServerIdentity evoSTS
- To disable HMA run Set-CsOAuthConfiguration -ClientAuthorizationOAuthServerIdentity $null
Enable Hybrid Modern Authentication for Exchange (EWS Connectivity)
- Run the following cmdlets to gather the URL’s that need to be added in AAD.
- Get-MapiVirtualDirectory | FL server,*url*
- Get-WebServicesVirtualDirectory | FL server,*url*
- Get-OABVirtualDirectory | FL server,*url*>
- Check the SSL certificates assigned to Exchange Web Services to make sure all required names are considered for inclusion.
- Connect to the AAD tenant.
- For Exchange-related URL’s, execute the following command:
- $x= Get-MsolServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000
- $x.ServicePrincipalnames.Add(“https://mail.shuc.uk/”)
- $x.ServicePrincipalnames.Add(“https://autodiscover.shuc.uk/”)
- $x.ServicePrincipalnames.Add(“https://azexchange.shuc.uk/”)
- Set-MSOLServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000 -ServicePrincipalNames $x.ServicePrincipalNames
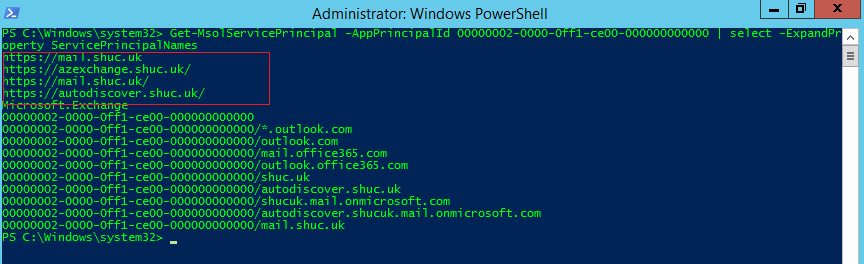
- Run Get-MsolServicePrincipal -AppPrincipalId 00000002-0000-0ff1-ce00-000000000000 | select -ExpandProperty ServicePrincipalNames
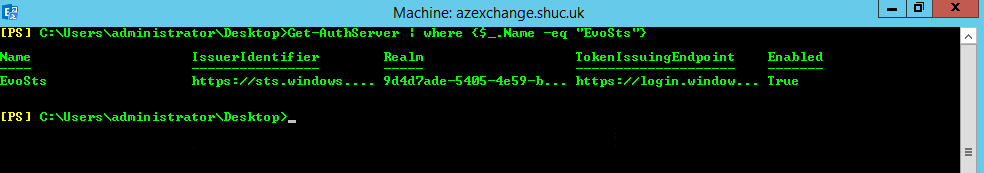
- Validate the EvoSts authentication provider is present using the Exchange Management Shell (Note: this is created by the Hybrid Configuration Wizard)
- Get-AuthServer | where {$_.Name -eq “EvoSts”}
- If the EvoSts entry is not present download and execute the latest version of the Hybrid Configuration Wizard.
- Ensure OAuth is enabled in Exchange on all the virtual directories Outlook might use.
- Get-MapiVirtualDirectory | FL server,*url*,*auth*
- Get-WebServicesVirtualDirectory | FL server,*url*,*oauth*
- Get-OABVirtualDirectory | FL server,*url*,*oauth*
- Get-AutoDiscoverVirtualDirectory | FL server,*oauth*
- Set the EvoSts authentication provider as the default provider by running: Set-AuthServer EvoSTS -IsDefaultAuthorizationEndpoint $true
- Enable the OAuth client feature for Windows Outlook: Set-OrganizationConfig -OAuth2ClientProfileEnabled $True
Intune Configuration
The following link here was used to verify the Mobile Application Management policy configuration. MDM device management was not enabled for the demo user.
- The MAM policy was configured to target Skype for Business & Microsoft Teams.
- Pin Lock was enabled in the MAM policy. All other MAM policy settings were left at their defaults.
- Security Group “MAM_ConditonalAccess_Users” was targeted by the MAM policy.
Conditional Access Policy
A CA policy was enabled so that Skype for Business/Exchange on-premises Android users are targeted specifically for MFA.
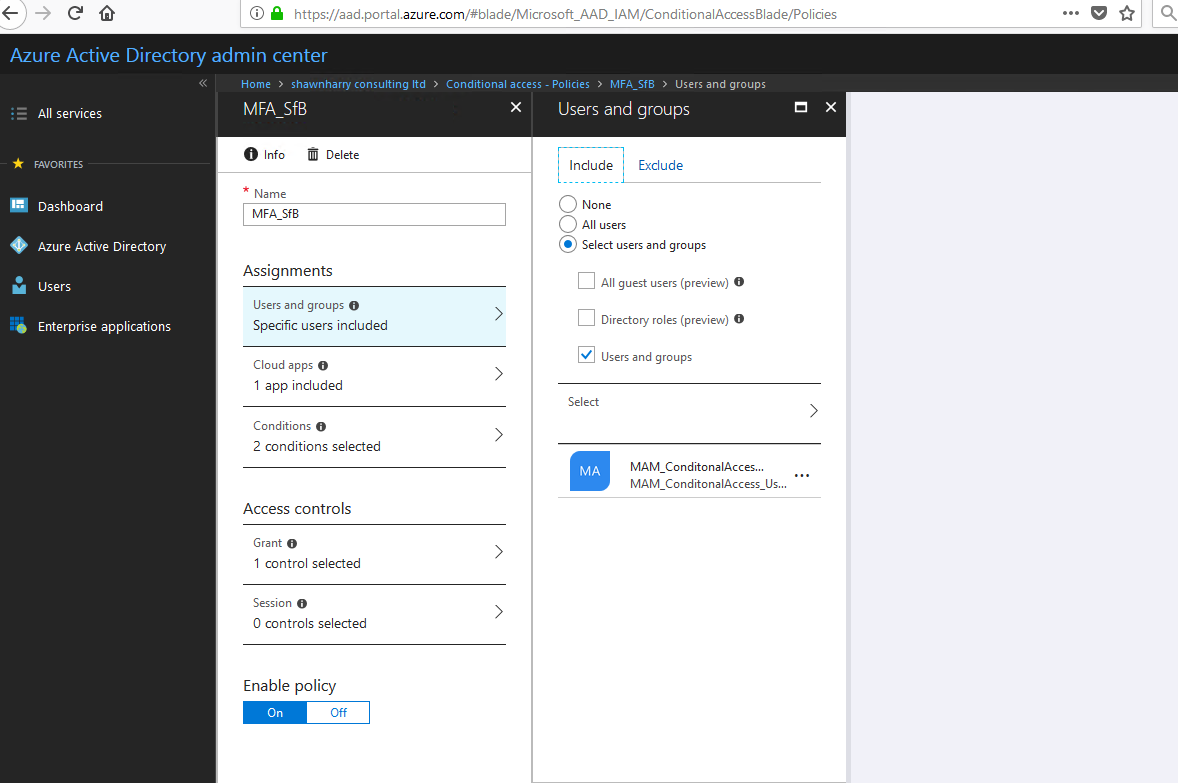
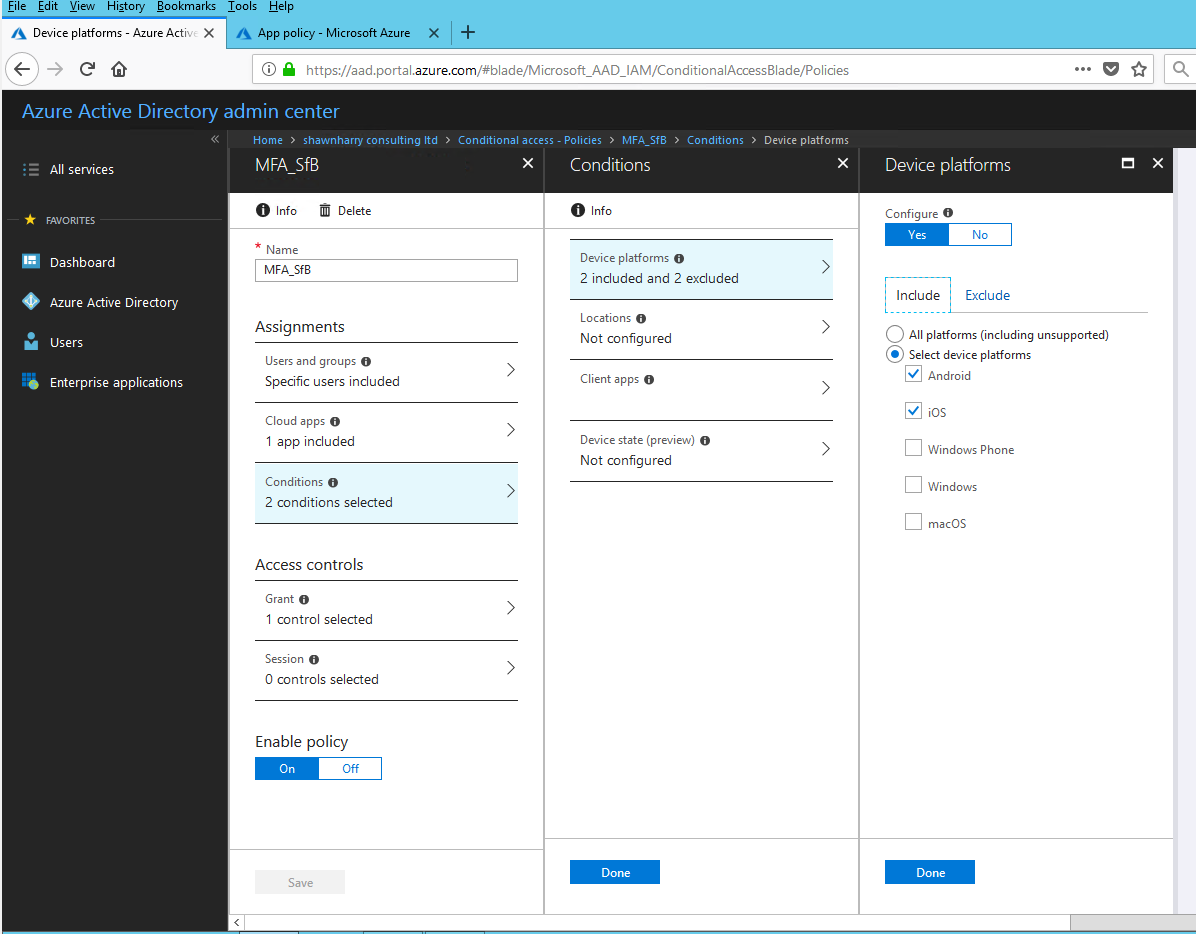
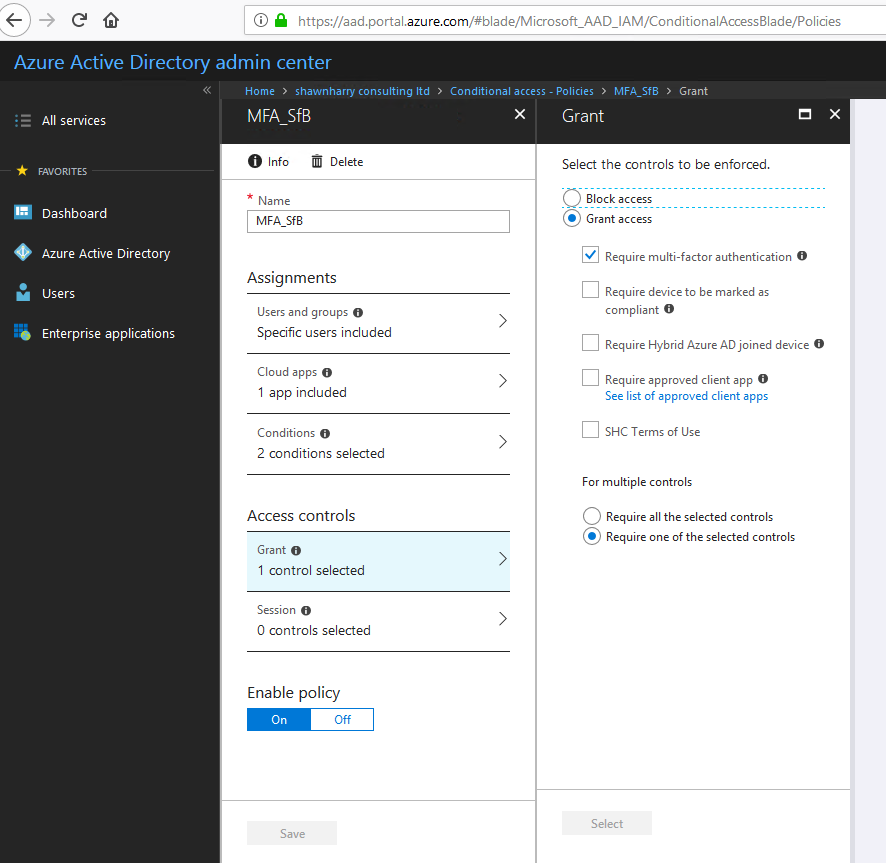
User Login Experience
- SfBS homed users needs to download and install the Intune Company Portal App.
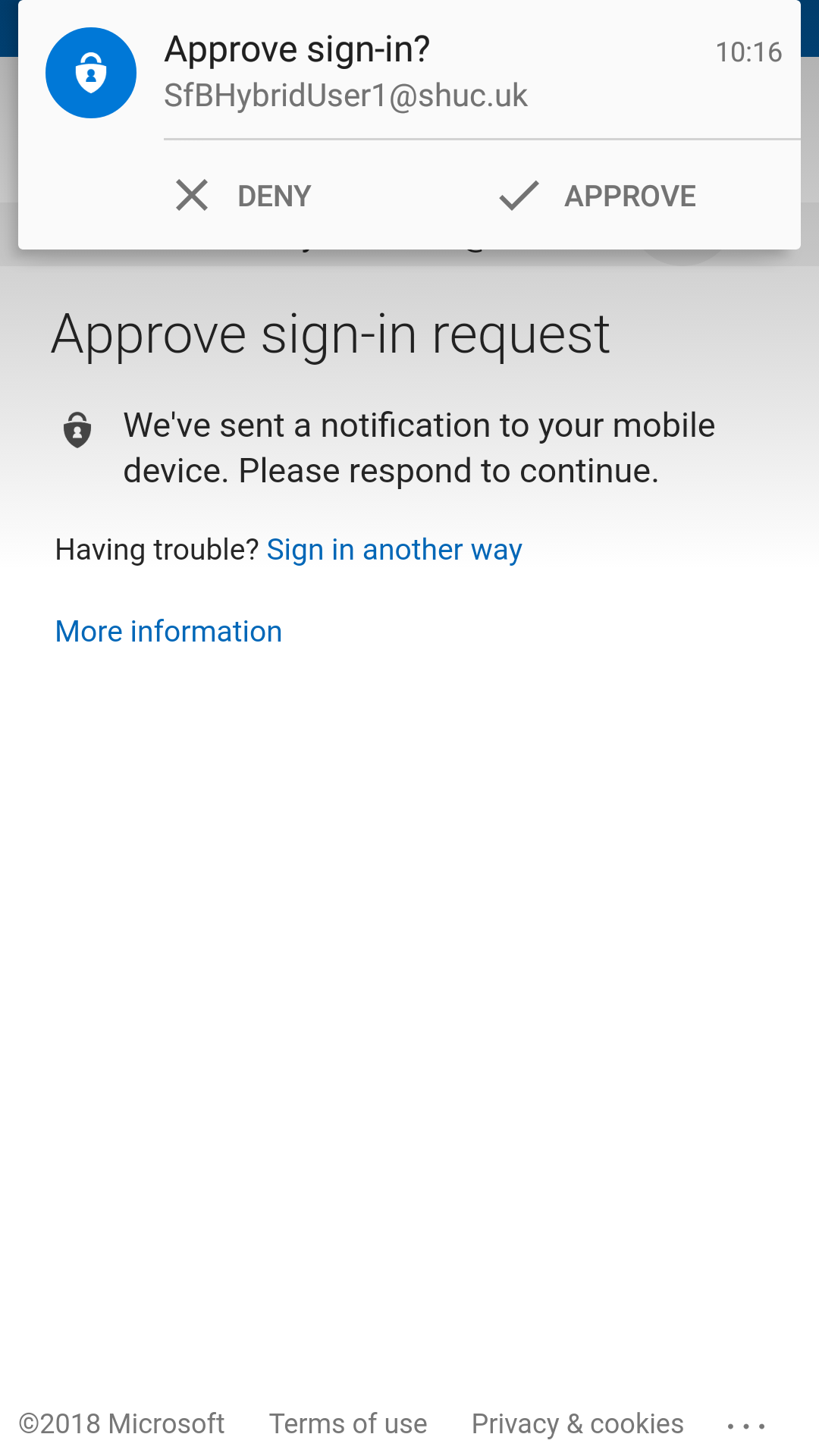
- Microsoft Authenticator App was used for the demo (Other MFA methods are possible and can be selected by the user by logging into https://myapps.microsoft.com Select Profile > Additional security verification.
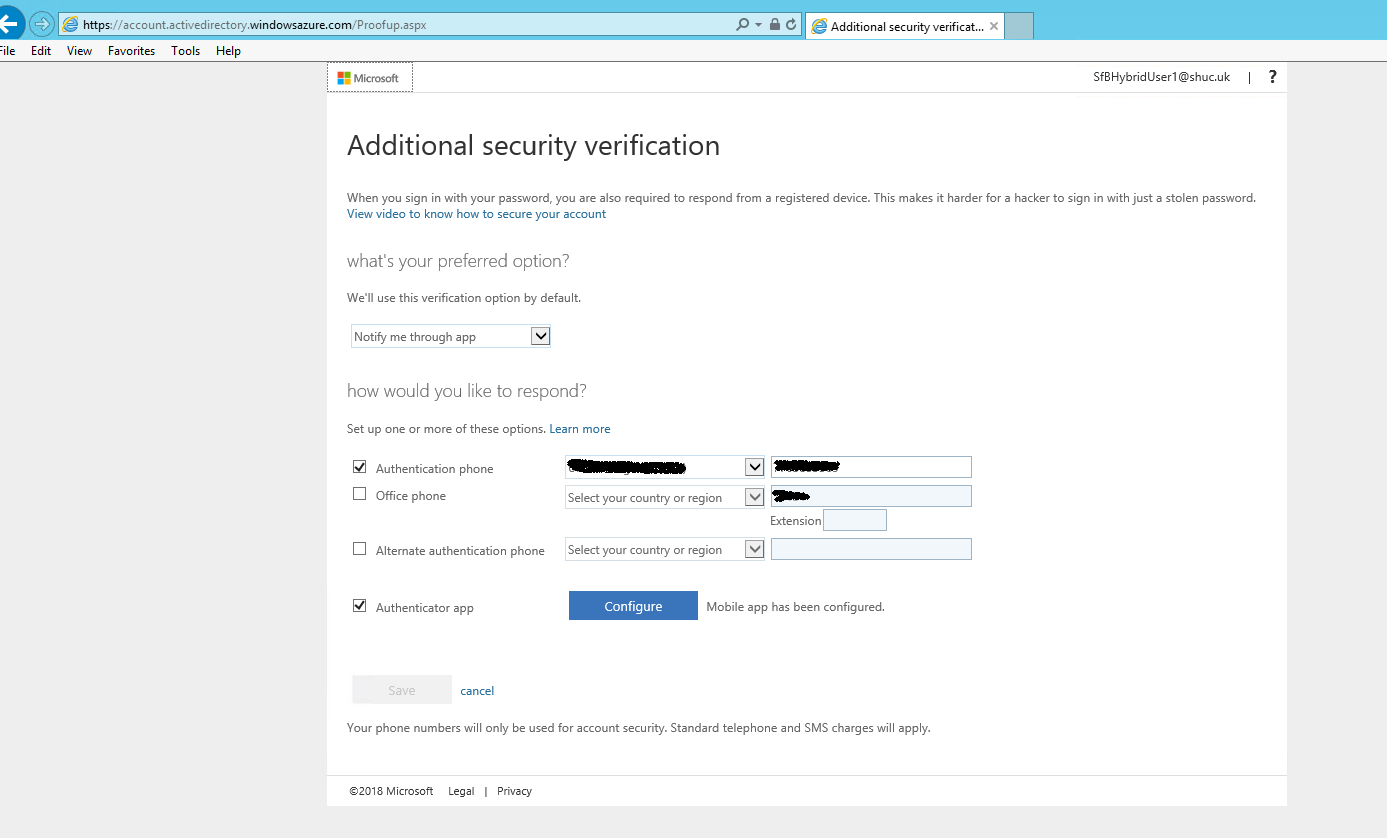

_____________________________________________________________________________________________________________________________________

_____________________________________________________________________________________________________________________________________
- Microsoft Authenticator was installed on the same test device for convenience.
_____________________________________________________________________________________________________________________________________
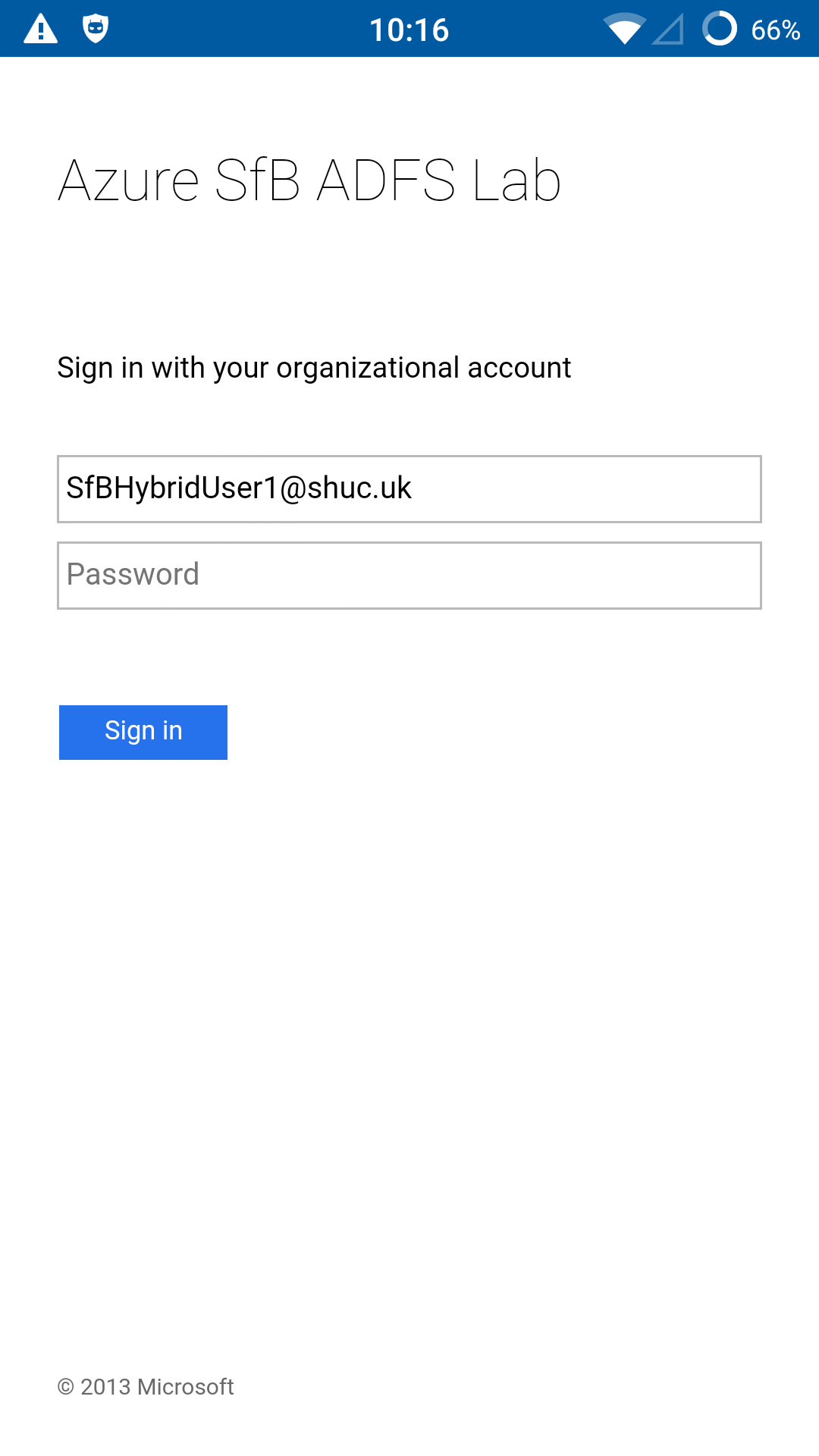
- Note the same Skype for Business credentials were used to logon to EWS. If MA is not enabled on Exchange Server and Exchange Online the user will be prompted to enter credentials and will use whatever authentication protocol is available to authenticate against EWS, example NTLM.
Completed in Azure Lab. Demo user was licensed for Intune & Azure AD Premium P1. Users homed on SfBS do not need to be licensed for SfBO.


