24 Aug How to Set up Azure AD Certificate-Based Authentication (CBA) for Skype for Business Online (Android)
Setting up CBA is already covered in detail here: –
This post covers my notes and findings on how to configure CBA as the deployment and architecture is relatively complex.
Topology
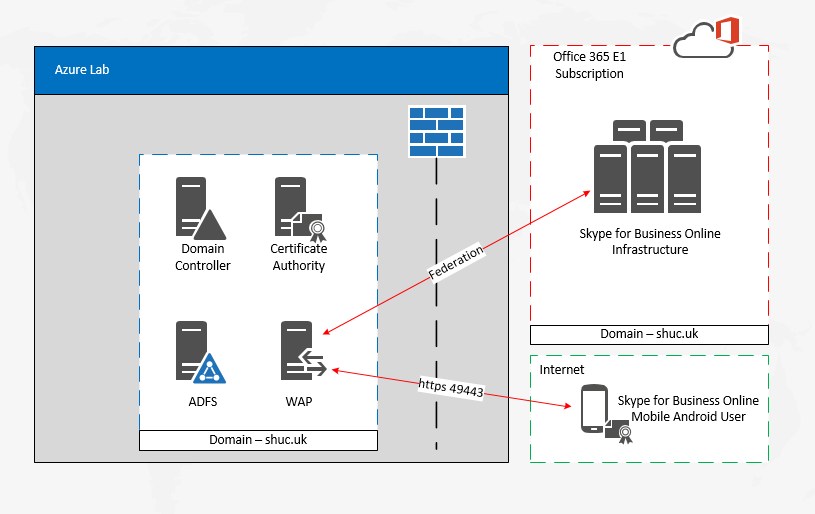
Certificate Based Authentication for SfBO mobile users is provided by a combination of ADFS and the on premises Certificate Authority whilst leveraging federation.
Background
The purpose of this lab was to understand the steps required for enabling CBA for SfBO specifically. The ability to login to SfB Mobile without using a username password combination is often a sought after configuration for large businesses with concerns around security or security policies that do not allow the use of corporate credentials over the internet. As SfB Mobile by default uses NTLM for both server & online CBA for SfBO users may be a suitable solution to this problem if MFA isn’t possible.
Note: CBA is not supported at present for SfB Server. See topology support for CBA: – https://technet.microsoft.com/en-us/library/mt803262.aspx
CBA is a topology only suitable for customers using SfBO or Exchange hybrid as the on premises architecture required to enable this capability would already be deployed. Conversely it is also possible providing a federation trust with O365 is configured as SfBO hybrid is not a mandatory requisite although federation with O365 is.
This post assumes Active Directory, Active Director Federation Services, a Web Application proxy to publish ADFS (EG WAP) and a Windows Certificate Authority are already configured. For the purpose of these deployment notes Azure Lab was used.
An MDM was not available in this lab to enroll certificates on the Android device used for testing. So, the root and user (Client Certificate) were exported via the CA and imported manually into the Android Phone.
Configuration Notes
Android
This link can be ignored. Whilst the Serial and Issuer claims need to be created so a certificate can be revoked successfully this is a requirement for both Android and iOS.
In addition the following cmdlet as suggested by this link does not need to be ran. Set-MSOLDomainFederationSettings -domainname shuc.uk -PromptLoginBehavior Disabled.
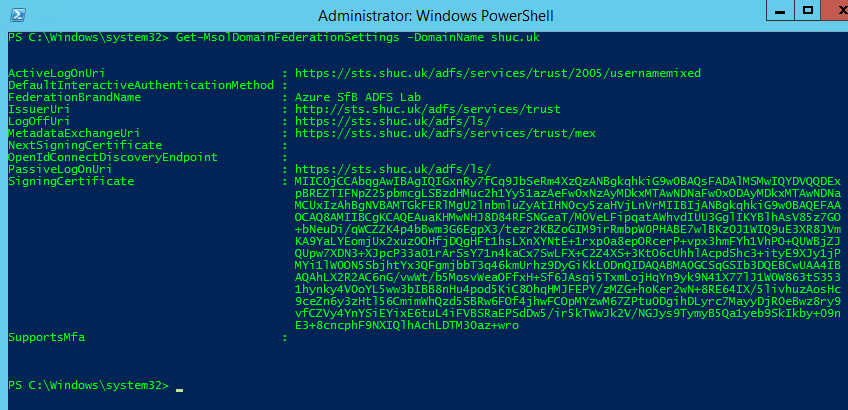
Note: – The -PromptLoginBehavior parameter is not available under the Set-MSOLDomainFederationSettings cmdlet. This paramter is still listed here: – https://docs.microsoft.com/en-us/powershell/module/msonline/set-msoldomainfederationsettings?view=azureadps-1.0 which likely needs updating.
Incidentally Microsoft Teams is also supported for CBA. This was not tested.
Certificate Revocation List
By default a CRL is not configured when deploying a CA. A CRL was configured on the CA using this link here:- https://blogs.technet.microsoft.com/nexthop/2012/12/17/updated-creating-a-certificate-revocation-list-distribution-point-for-your-internal-certification-authority/ Port 80 was opened on the Azure (CA) VM to allow the CRL to be accessible over the internet and internal and external DNS updated for crl.shuc.uk
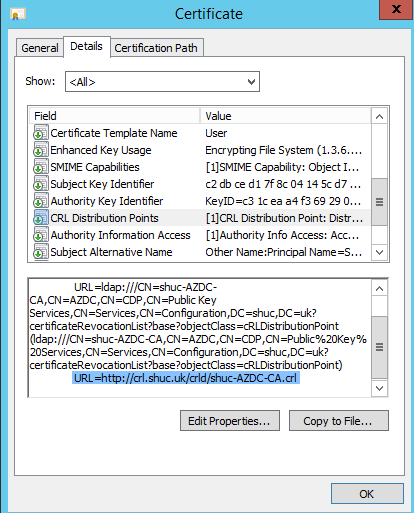
With the new CRL published the CRL is now available and included in the CDP on the users Client Certificate.
Enable Certificate Authentication in ADFS
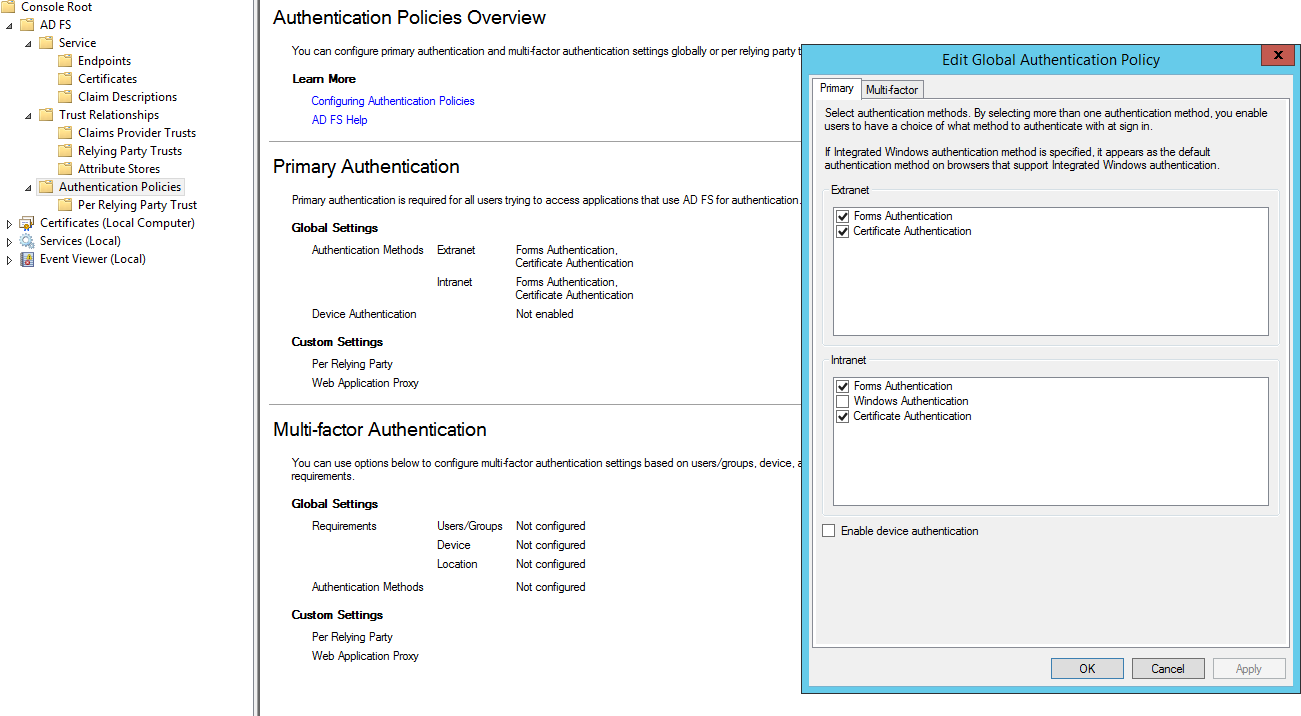
This is an important step. If this is not enabled the ability to select a certificate is not shown in the ADFS logon page.
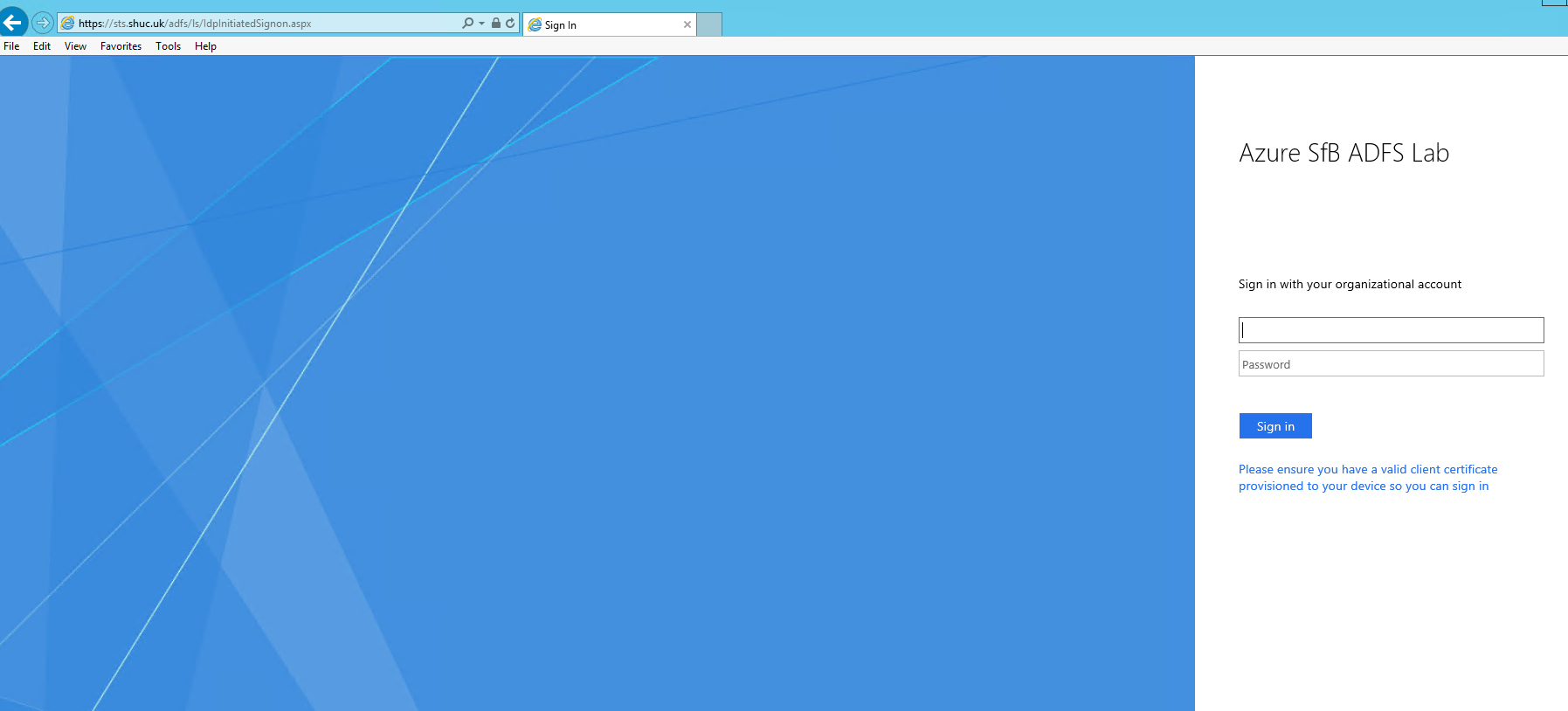
Set-AdfsAuthenticationProviderWebContent -Name CertificateAuthentication -DisplayName “Please ensure you have a valid client certificate provisioned to your device so you can sign in”. This is to change the wording on the ADFS logon page to something more user friendly.
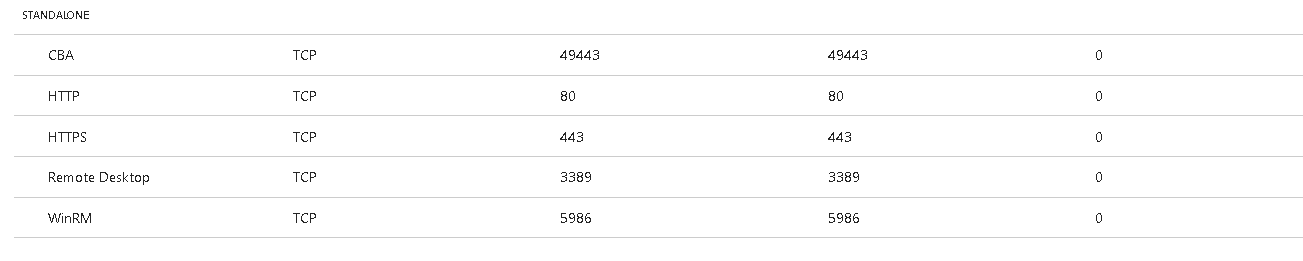
Firewall
Authentication requests from SfB Mobile clients connected to the internet are completed over port 49443.
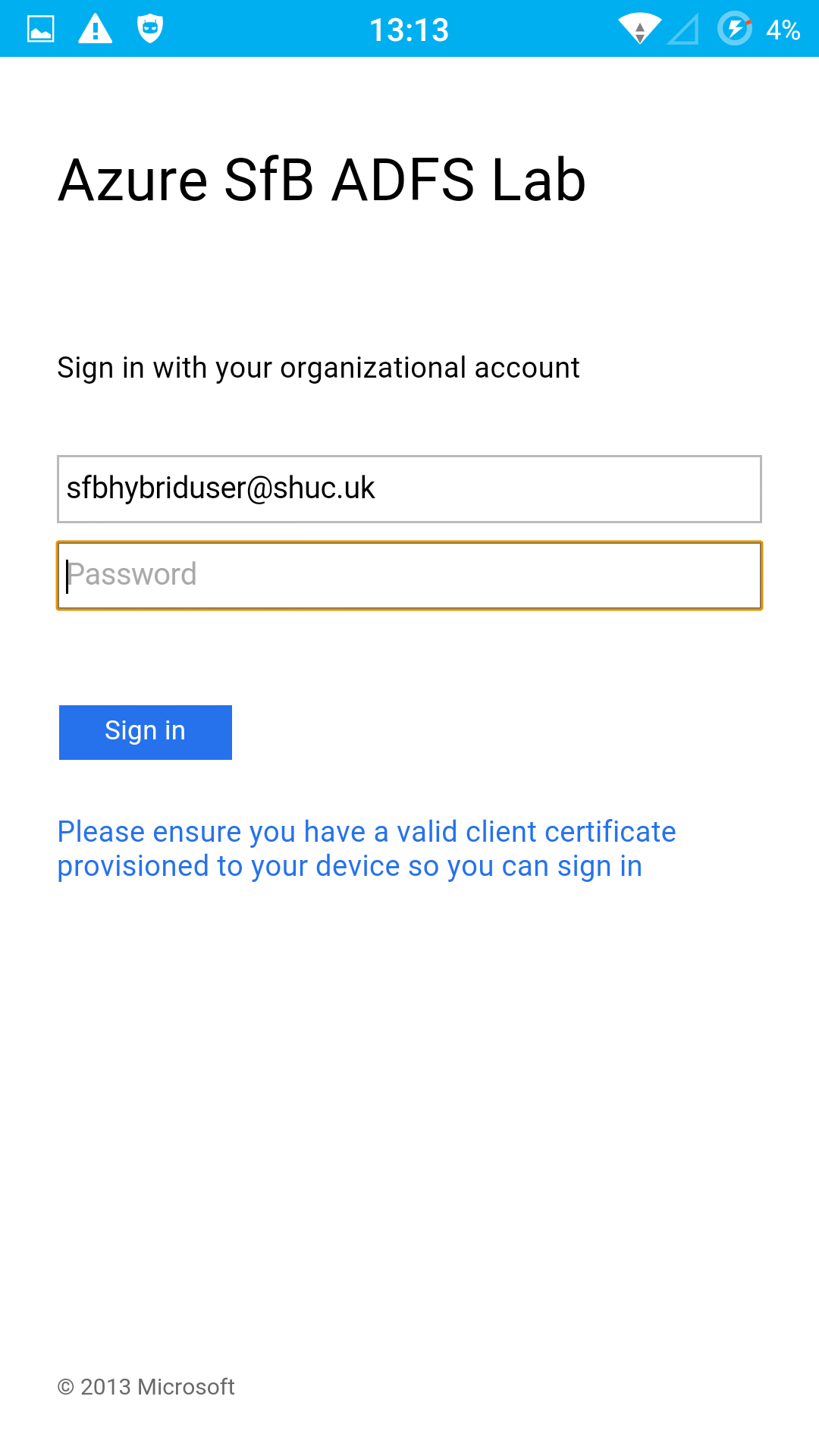
Login Experience

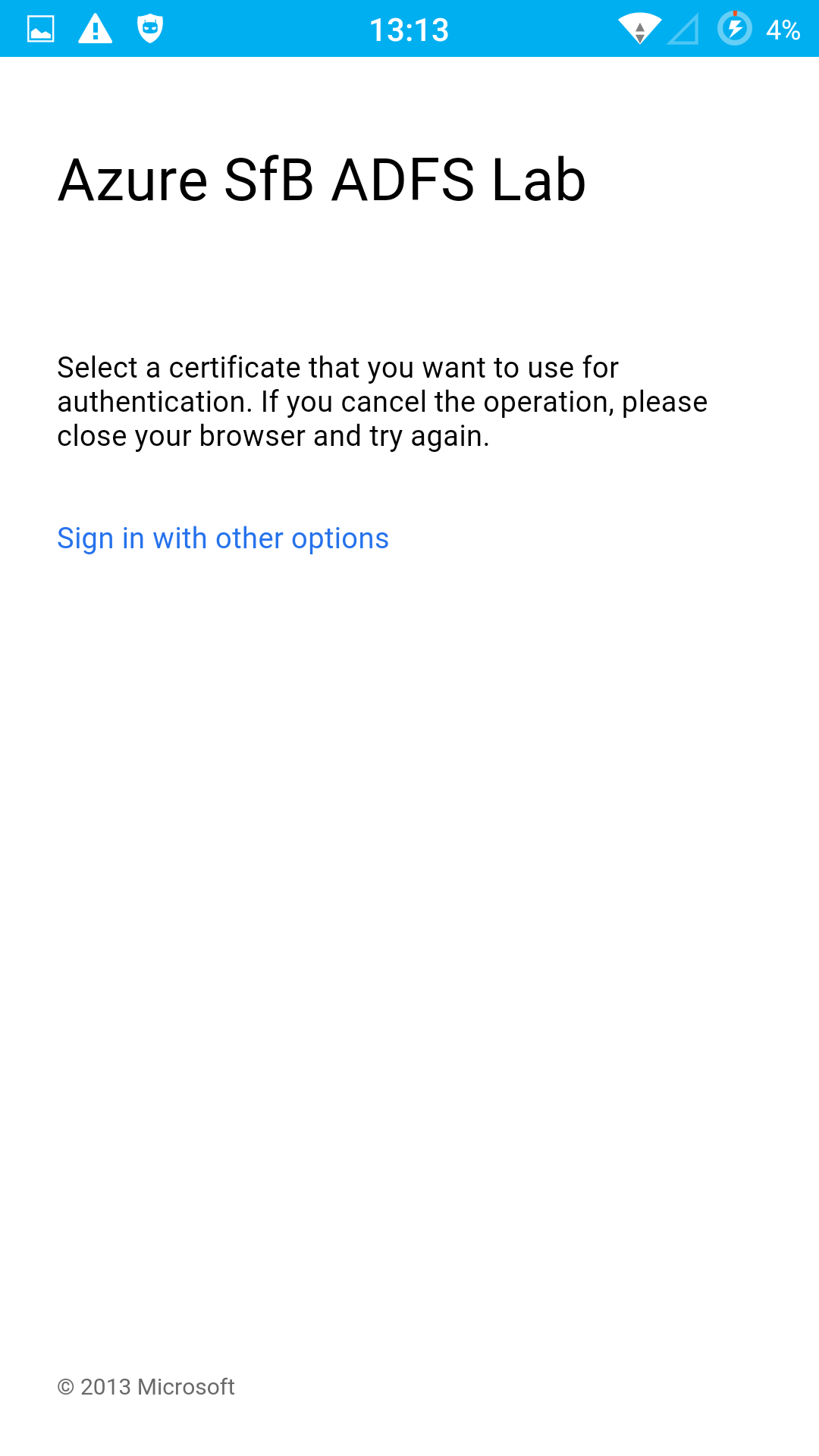
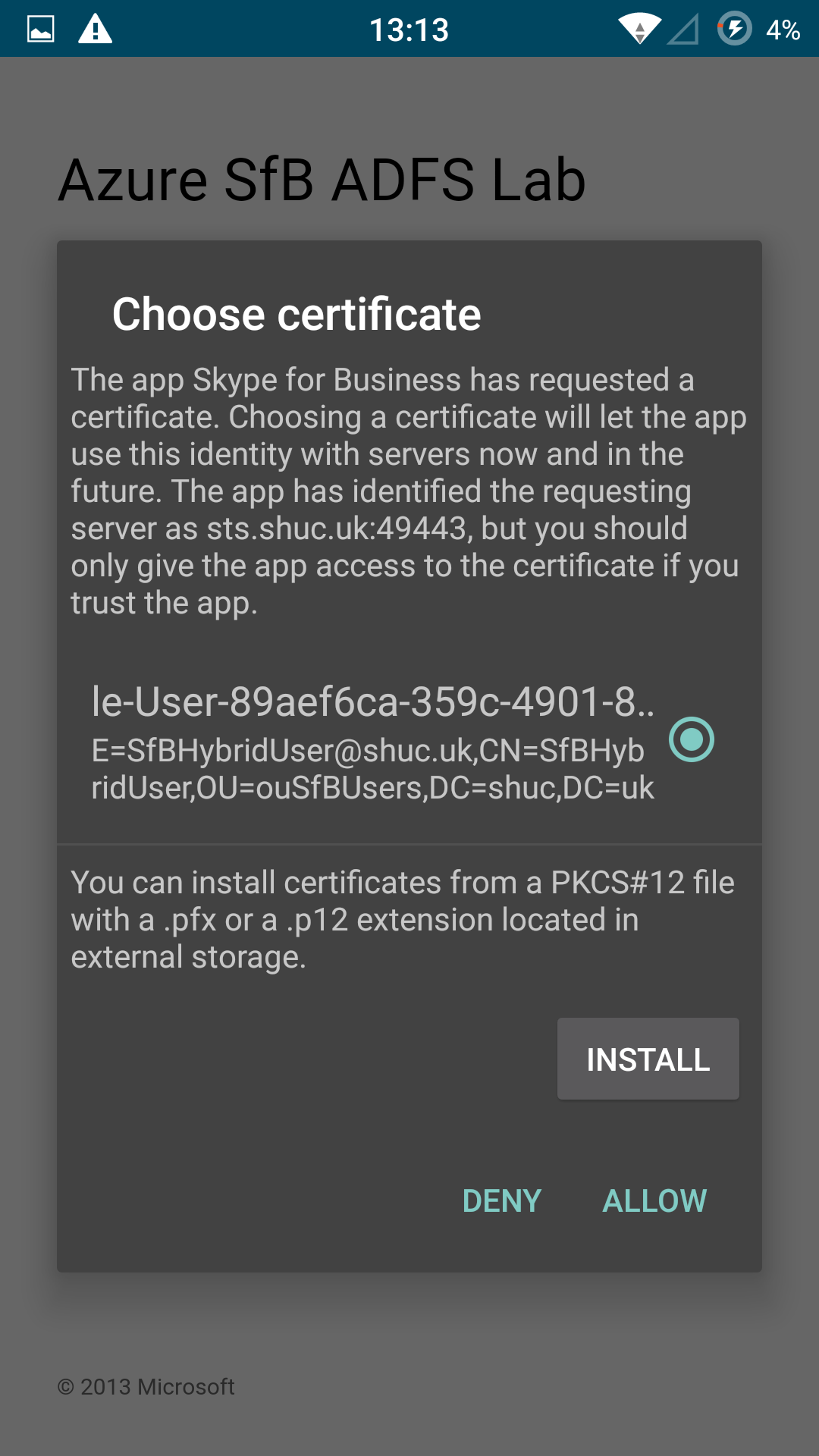
Drawbacks
On premise servers are required EG ADFS/WAP (Reverse Proxy)/ADDC/CA to enable CBA. It is currently not possible to enable CBA if using a pure O365/SfBO deployment.
Azure IAAS may be a suitable option to reduce on premises server footprint but comes with the associated cost for an Azure subscription. (For testing purposes, this lab was completed entirely in Azure with SfBO hybrid).


