17 Mar Whitelisting Skype for Business URLs when using the BlueCoat Unified Agent and Direct Access
Summary: The topology consisted of Skype for Business Server deployed alongside Direct Access. To preserve call quality ALL SfB traffic was not be tunnelled by DA or any other solution that deployed a VPN secure tunnel as did the Blue Coat Unified Agent.
The following article covers extensively why SfB/Lync traffic should not be subject to a VPN tunnel:-
https://blogs.technet.microsoft.com/nexthop/2011/11/14/enabling-lync-media-to-bypass-a-vpn-tunnel/
The BCUA is a small utility that provides a Cloud Proxy service for remote users so http(s) based web traffic is proxied via the Cloud Service.
Symptom: The BCUA was forcing registration over the DA VPN tunnel rather than over the SfB Edge server for the default SIP domain name.
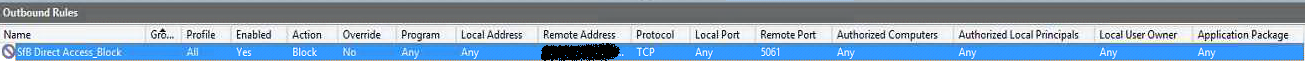
Resolution: To accommodate SfB server and prevent logins from being tunnelled over DA the exclusions in figure 1 below were required.
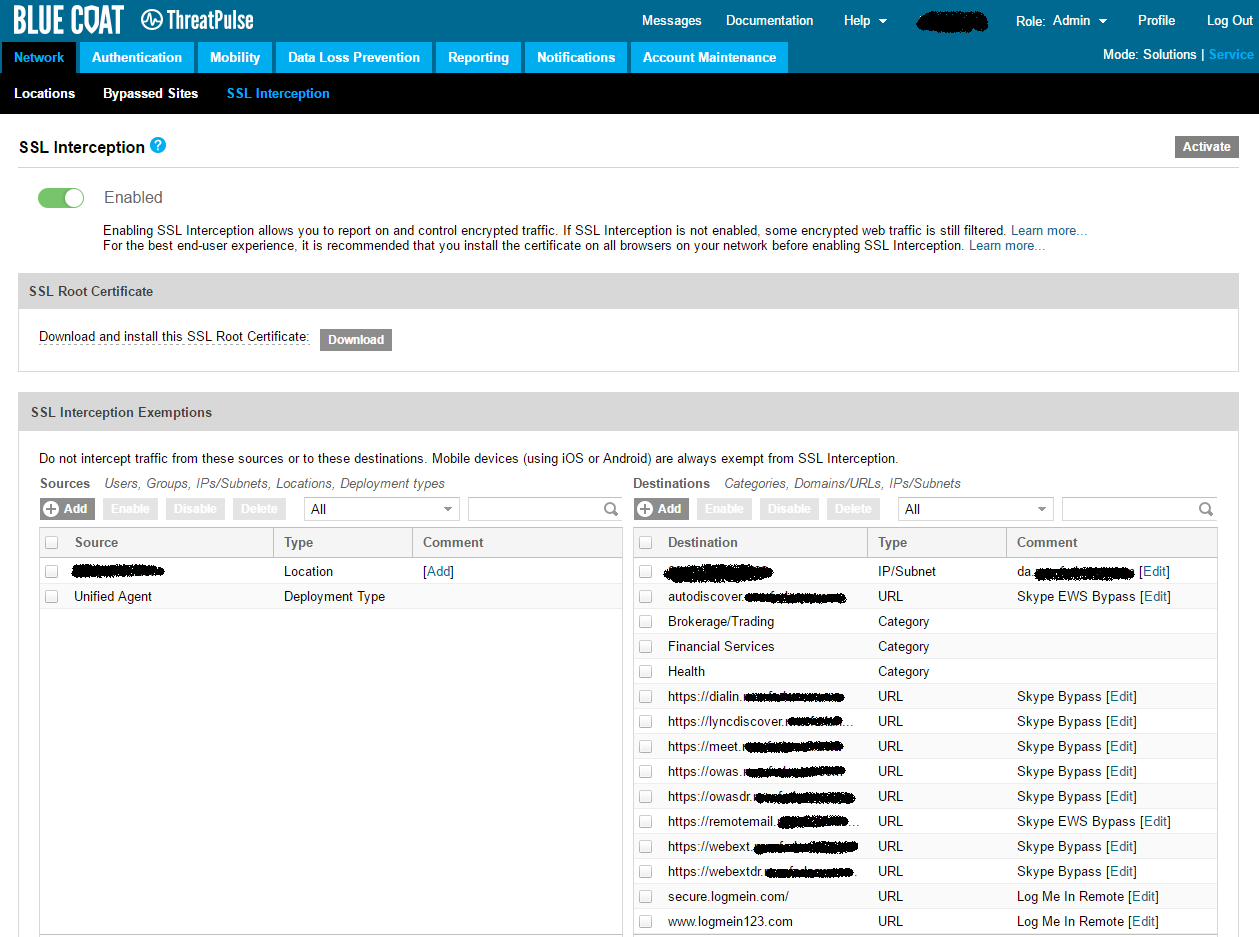
Figure 1
By specifying this rule all SfB traffic client side was not intercepted by the BCUA. The following Windows FW rule must also be created on all DA servers so the DA server(s) cannot communicate with the SfB Front End Server on port 5061 SIP TLS. This prevents registrations over DA by the SfB client if the first accessible DNS record and discoverable endpoint is ‘lyncdiscoverinternal.domain.com’.